Docker Network commands
# docker network ls NETWORK ID NAME DRIVER SCOPE 234dbbb8d381 bridge bridge local e23bbf6e6a54 docker-hive_default bridge local e284120f22c7 host host local 019daa8ddd49 none null local
$ docker ps --format "table {{.ID}}\t{{.Status}}\t{{.Names}}"
CONTAINER ID STATUS NAMES
608fe6f7a1c4 Up About an hour docker-tutorial
Docker Example
To illustrate this, we will use a Hive and Hadoop environment, containing 5 Docker Containers from – https://github.com/mesmacosta/docker-hive.
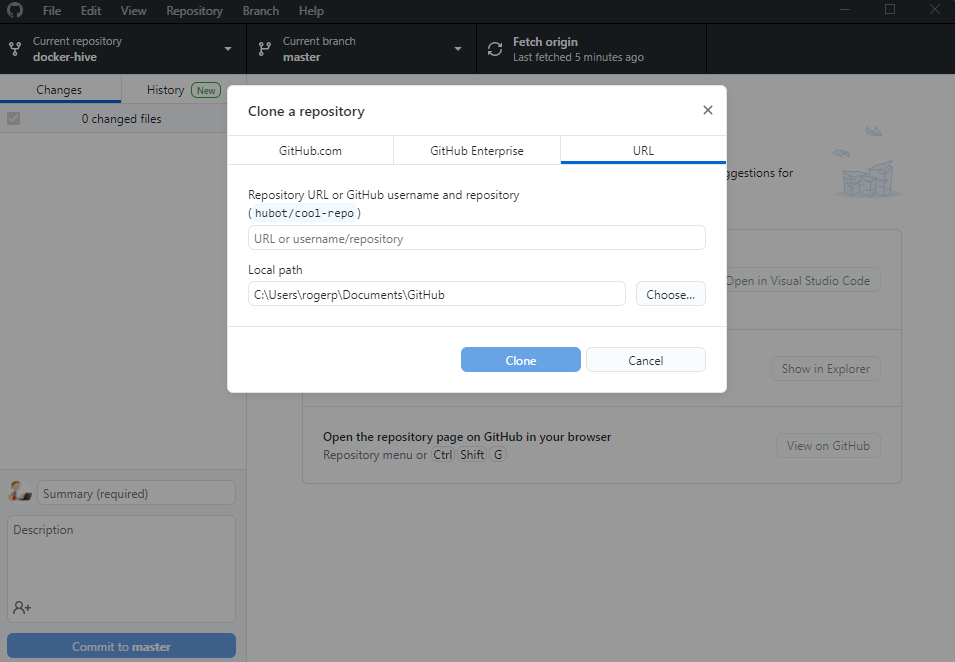
Since I am on windows, I use Github desktop.
Launch Github desktop and then go to File >> Clone Repository >> URL.
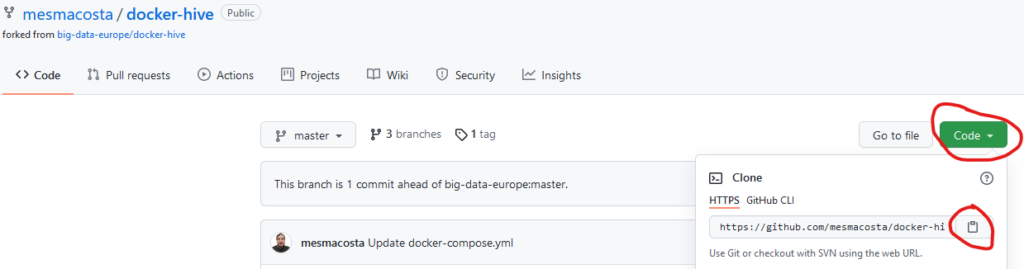
Go to https://github.com/mesmacosta/docker-hive – Click on Code > Copy. Paste URL into Github Desktop. Click Clone.
Now open command prompt or Powershell – AS ADMINISTRATOR – and go to the directory where the docker files are located. In my case its in Documents > Github > docker-hive.
Now let’s start up those containers:
# docker-compose up -d
Note: If you receive this error:
Error response from daemon: Ports are not available: listen tcp 0.0.0.0:50070: bind: An attempt was made to access a socket in a way forbidden by its access permissions.
Run this in command prompt or PS:
net stop winnat net start winnat
We can see 5 containers:
>docker ps --format "table {{.ID}}\t{{.Status}}\t{{.Names}}"
CONTAINER ID STATUS NAMES
30714f65fc36 Up 2 minutes docker-hive_hive-metastore_1
cc281caa92ba Up 2 minutes docker-hive_hive-server_1
66aed41cdc5e Up 2 minutes docker-hive_hive-metastore-postgresql_1
d90c10f7cfe6 Up 2 minutes (healthy) docker-hive_datanode_1
baf998183015 Up 2 minutes (healthy) docker-hive_namenode_1
Next let’s check our Docker networks:
>docker network ls NETWORK ID NAME DRIVER SCOPE 234dbbb8d381 bridge bridge local d438c2ba7c56 docker-hive_default bridge local e284120f22c7 host host local 019daa8ddd49 none null local
By default docker compose sets up a single network for your app. And your app’s network is given a name based on the “project name”, originated from the name of the directory it lives in.
So since our directory is named docker-hive, this explains the new network.
Getting more information.
Docker inspect can retrieve low-level information on Docker objects. You can pick out any field from the returned JSON.
Let’s get the IP Address from the dockerhive_datanode.
>docker ps --format "table {{.ID}}\t{{.Status}}\t{{.Names}}"
CONTAINER ID STATUS NAMES
30714f65fc36 Up 2 minutes docker-hive_hive-metastore_1
cc281caa92ba Up 2 minutes docker-hive_hive-server_1
66aed41cdc5e Up 2 minutes docker-hive_hive-metastore-postgresql_1
d90c10f7cfe6 Up 2 minutes (healthy) docker-hive_datanode_1
baf998183015 Up 2 minutes (healthy) docker-hive_namenode_1
Get the container ID from the above command to find the following:
$ docker inspect -f '{{range.NetworkSettings.Networks}}{{.IPAddress}}{{end}}' d90c10f7cfe6
172.20.0.2
Docker Logs
How to check Docker logs
sudo docker logs
Get Docker Container:
# sudo docker ps --format "table {{.ID}}\t{{.Status}}\t{{.Names}}"
Now view the logs:
$ sudo docker logs d90c10f7cfe6
Docker Ports
$ docker container ls --format "table {{.ID}}\t{{.Names}}\t{{.Ports}}" -a
CONTAINER ID NAMES PORTS
a624f0ae744e cool_moore
a0d9f2b7ce84 zealous_mclean 0.0.0.0:80->80/tcp, :::80->80/tcp
docker inspect
This method allows one to return low-level information on the container or image.
Syntax
docker inspect Container/Image
Select IP
# docker inspect c52b91aa0dea | grep -i ip
Ports
docker inspect c52b91aa0dea | grep -i port