What are the top cache plugins for wordpress?
There are several popular cache plugins for WordPress, including:
Redis Object Cache – A persistent object cache backend powered by Redis. Supports Predis, PhpRedis, Relay, replication, sentinels, clustering and WP-CLI.
Panomity WP Cache – Provides an extremely simple full page cache of the homepage.
WP Fastest Cache – This is a lightweight and easy-to-use plugin that offers a range of caching options, including minification and Gzip compression.
W3 Total Cache – This is a comprehensive caching plugin that offers a range of caching options, including page caching, database caching, and object caching.
WP Super Cache – This is a popular caching plugin that offers a range of caching options, including page caching, gzip compression, and CDN support.
Comet Cache – This is a simple and easy-to-use caching plugin that offers features such as page caching, browser caching, and Gzip compression.
LiteSpeed Cache – All-in-one unbeatable acceleration & PageSpeed improvement: caching, image/CSS/JS optimization.
It’s worth noting that the effectiveness of a caching plugin can depend on your website’s specific setup and requirements, so it’s a good idea to experiment with different options to find the best fit for your site.
Let’s test a WordPress WooCommerce Site – CaptainsCBDShop.com.
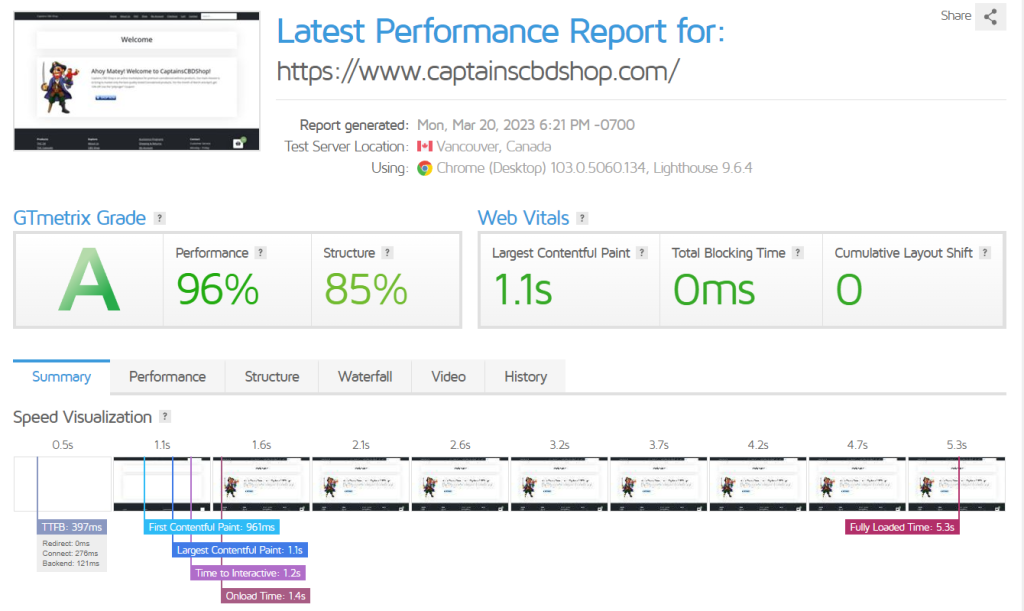
Without Cache Plugins – https://gtmetrix.com/reports/www.captainscbdshop.com/bwO9zBlZ/
In this test, we will test without any plugins.
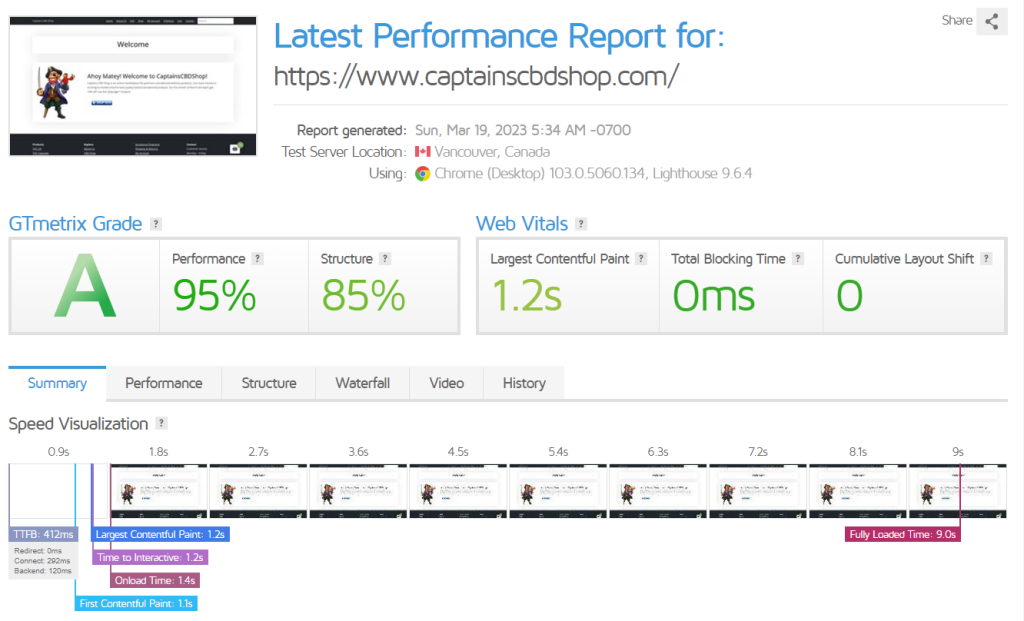
With Redis Object Cache
In this test, we set up redis and then installed the plugin in WordPress.
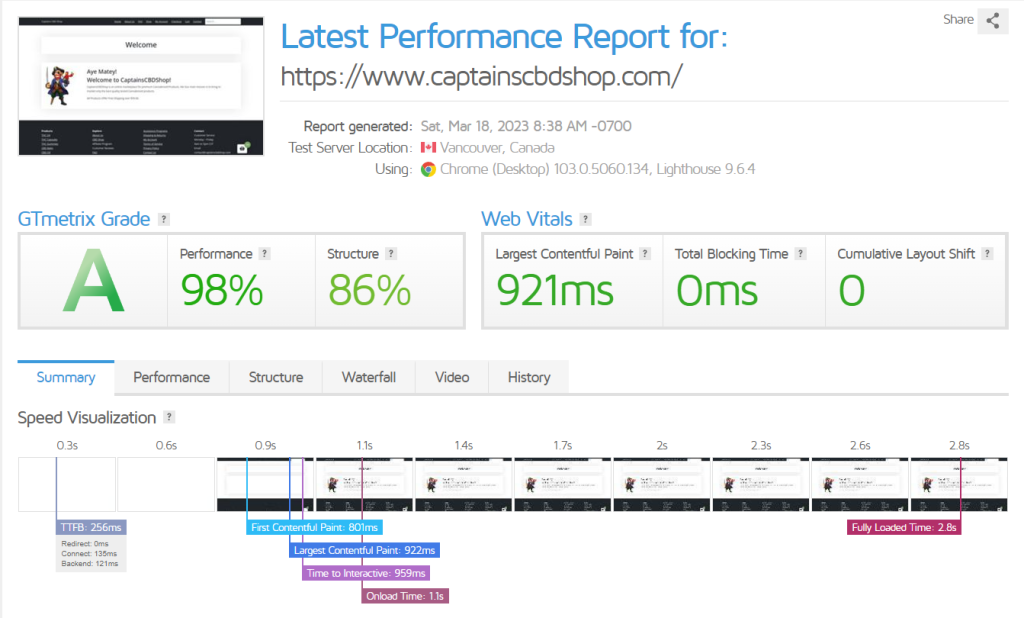
With Panomity WP Cache
In this test, we set up the Panomity WP Cache plugin.
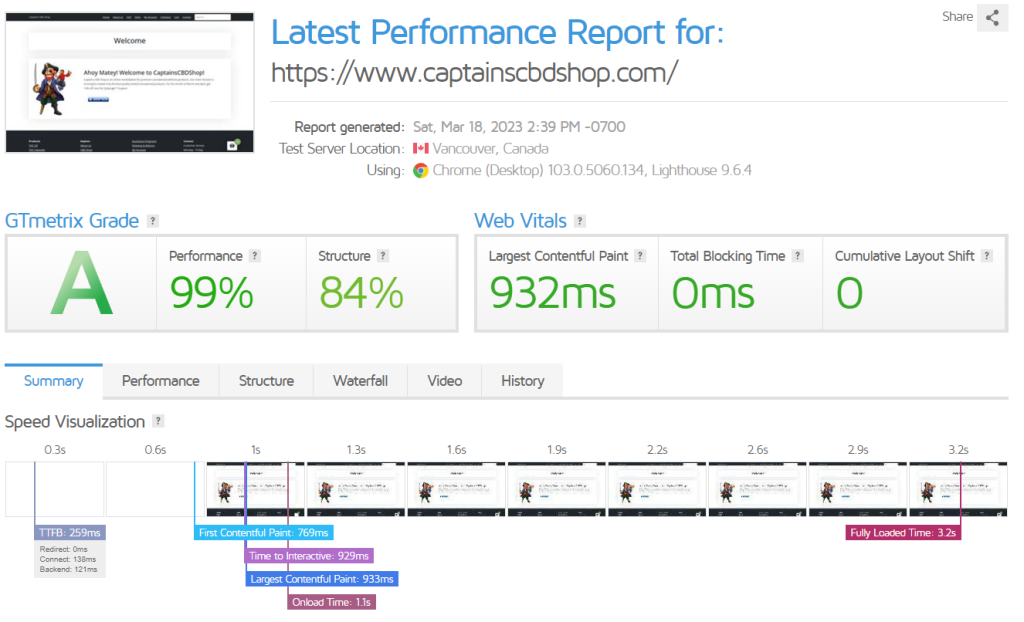
WP Fastest Cache
Here we test with WP Fastest Cache.
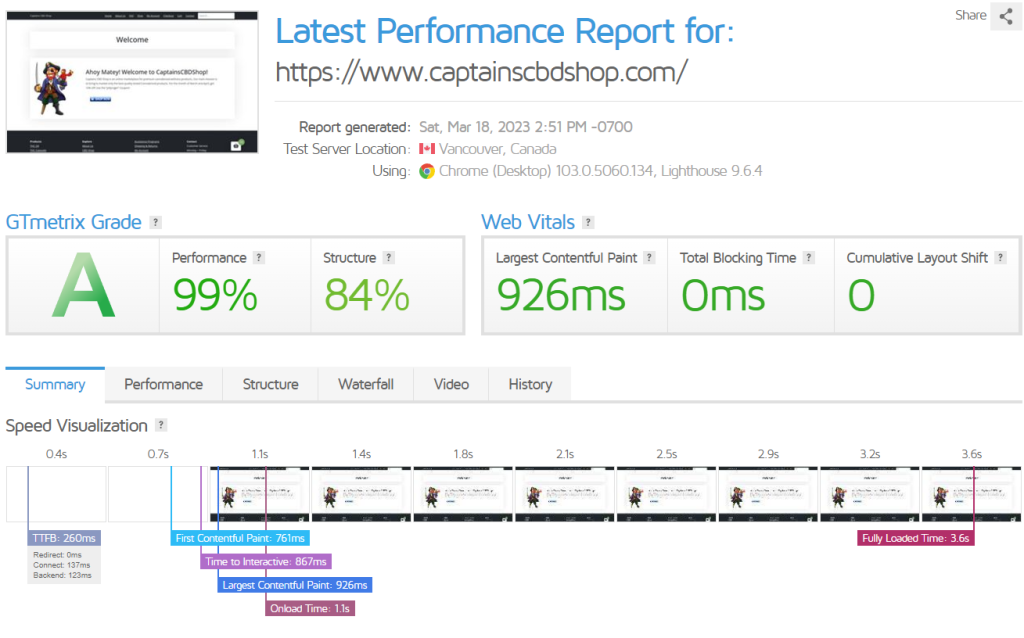
W3 Total Cache
Below we set up W3 Total Cache
W3 Total Cache has a cool setup where you can configure it.

Here are the test results after installation.