The dig command in Linux is used to perform DNS lookups and query DNS servers. Here are some common ways to use dig.
Category: DNS
If you ever set up a new domain hosting or migrate a domain to a new server, you will want to check to make sure that the changes are good before changing the DNS to the new server.
We often get asked this question a lot as in many cases, clients change the DNS before checking to see if there site actually works. This can lead to frustration, downtime and lost revenue and customers.
Dnsmasq is a lightweight, easy to configure, DNS forwarder and DHCP server. It is designed to provide DNS and optionally, DHCP, to a small network. It can serve the names of local machines which are not in the global DNS.
Source: https://wiki.debian.org/dnsmasq
Basic DNS Setup
First things first, let’s install the package:
apt-get update apt-get install dnsmasq
If your goal was to set up a simple DNS server, you just succeeded. To test it, use your favorite DNS lookup tool pointed at localhost:
dig debian.org @localhost ; <<>> DiG 9.16.33-Debian <<>> debian.org @localhost ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 23056 ;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;debian.org. IN A ;; ANSWER SECTION: debian.org. 300 IN A 149.20.4.15 debian.org. 300 IN A 130.89.148.77 debian.org. 300 IN A 128.31.0.62 ;; Query time: 44 msec ;; SERVER: ::1#53(::1) ;; WHEN: Thu Sep 29 16:26:24 CDT 2022 ;; MSG SIZE rcvd: 87
or
nslookup debian.org localhost Server: localhost Address: ::1#53 Non-authoritative answer: Name: debian.org Address: 128.31.0.62 Name: debian.org Address: 130.89.148.77 Name: debian.org Address: 149.20.4.15 Name: debian.org Address: 2001:67c:2564:a119::77 Name: debian.org Address: 2603:400a:ffff:bb8::801f:3e Name: debian.org Address: 2001:4f8:1:c::15
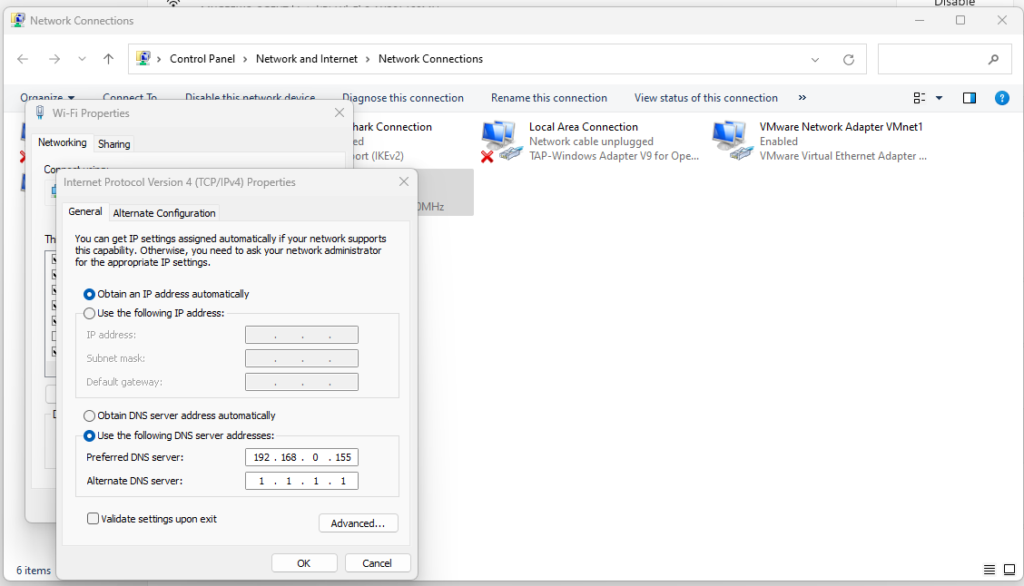
By default, DNS is configured to forward all requests to your system’s default DNS settings. In case you didn’t know, these are stored in the /etc/resolv.conf
To add names, simply add them to your /etc/hosts file.
nano /etc/hosts 192.168.0.155 ipgw.io
dig ipgw.io @localhost ; <<>> DiG 9.16.33-Debian <<>> ipgw.io @localhost ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 53022 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;ipgw.io. IN A ;; ANSWER SECTION: ipgw.io. 0 IN A 192.168.0.155 ;; Query time: 0 msec ;; SERVER: ::1#53(::1) ;; WHEN: Thu Sep 29 16:31:02 CDT 2022 ;; MSG SIZE rcvd: 52
Choosing Your Interfaces
One you will probably want to do is tell dnsmasq which ethernet interface it can and cannot listen on, as we really don’t want it listening on the internet. Around line 69 of the /etc/dnsmasq.conf file, you will see:
#interface=
By default, DHCP is turned off.
Now change your dns on the IPv4 to your dnsmasq address server and your DNS server like Cloudflare.
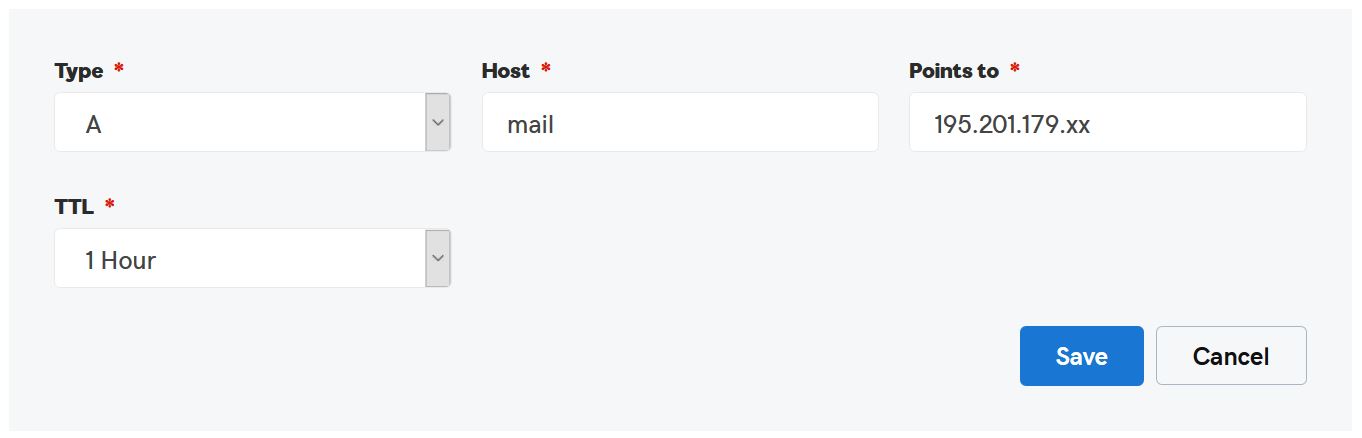
This article describes how to add an MX record to Godaddy if the DNS is hosted at Godaddy.
Create an A record for “mail”. Point the record to the primary IP where the mail will be hosted. This can be the same IP as the website or a different IP if mail in on a different server.
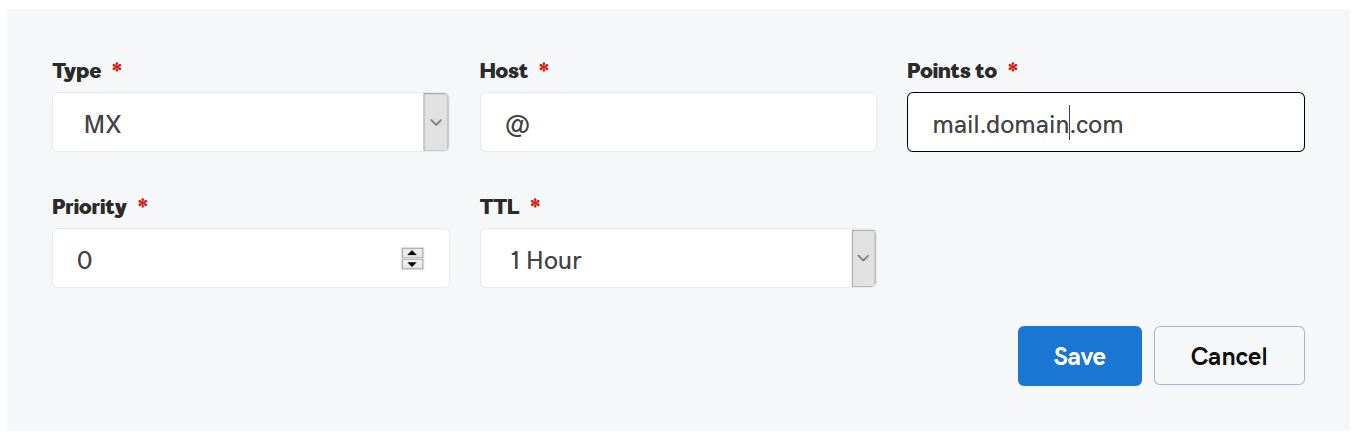
Now create the MX record. Replace “domain” with your actual domain name.
Allow for DNS propigation. Check the DNS at:
https://www.whatsmydns.net
Amazonon DMARC (http://sesblog.amazon.com/post/Tx22ZELXSSZRYZR/What-is-DMARC-and-should-you-use-it).
This Google article is also helpful: https://support.google.com/a/answer/2466563?hl=en
If you scroll down to the ‘Example records’ section, you’ll see a number of examples on how to write the TXT record. Here’s an example of that record:
_dmarc.advancedmediawebs.com. 3600 IN TXT “v=DMARC1; p=quarantine; pct=5; rua=mailto:mark@domain.com”
# dig +short test.openresolver.com TXT @1.1.1.1 (IP of the server)
Other Information
Test your server for an open DNS resolver here:
Closing DNS Resolvers on Windows Server 2003/2008/2008 R2:
http://technet.microsoft.com/en-us/library/cc787602(v=ws.10).aspx
Windows Servers running Plesk:
http://kb.parallels.com/en/116463
Closing DNS Resolvers on Servers running Bind:
Configuring the rDNS for a linux server is easy. A windows server with plesk is a different story.
Plesk
I changed the hostname in the plesk Tools and Settings.
Rebooted the system. Then sent a test email. Here is the header:
Received: from WIN-QO7M1M92HBS.home
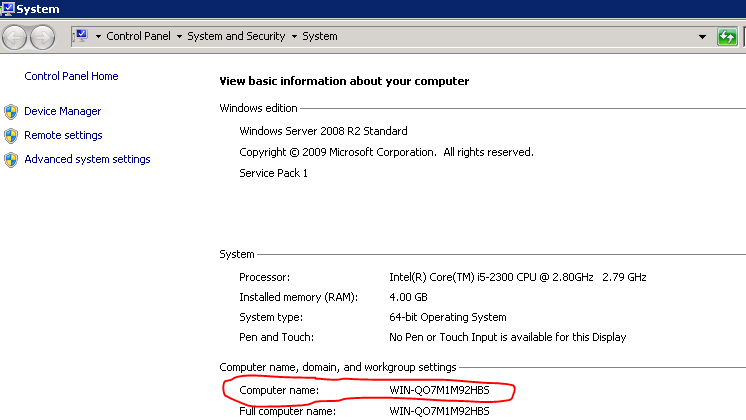
Humm…where is the new hostname? So I did some investigation. I checked the computername in windows:
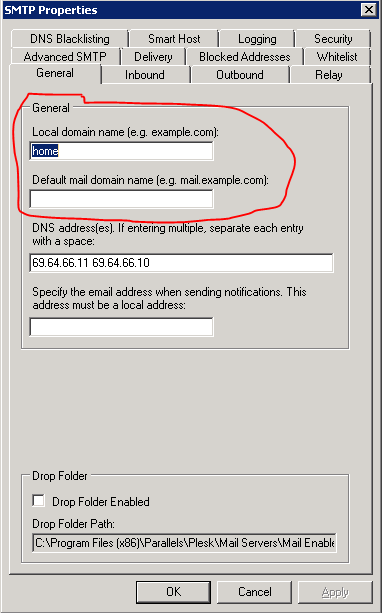
Then I checked the Mailenable settings > Services and Connectors > SMTP > properties.
So, the email received from name is a combination of the Windows computer name and the Mailenable Local domain name.
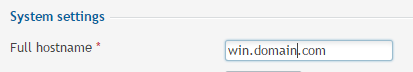
Now that I had this information, how do I give the mail server a valid hostname?
You would add the DKIM record as a txt record
Name: 122132._domainkey
Value: DKIM public key and options
To Disable Recursive DNS in the Parallels Plesk Panel
- Log in to the Parallels Plesk Panel as administrator.
- Click Tools & Settings.
- From the General Settings area, click DNS Template Settings.
- Click DNS Recursion.Select Localnets, and then click Ok.
For Windows Servers:
- Log in to your Server through a Remote Desktop Connection.
- From the Start menu, click Control Panel, Administrative Tools, then DNS.
- In the console tree, right-click the appropriate DNS server, and then click Properties.
- Click the Advanced tab.
- Under Server options, check Disable recursion, and then click OK.
- In the console tree, right-click the appropriate DNS server, and then click Clear Cache.
CentOS
# cd /etc # nano named.conf
Change this line
# recursion yes;
to
# recursion no;
Restart
# service named restart
Ubuntu
# nano /etc/bind/named.conf.options
Set up like this
// global options apply to external clients
options {
recursion no;
additional-from-auth no;
additional-from-cache no;
};
view "local" in {
// view options enable recursion only for local clients
match-clients { 172.16.45.80/23; 192.168.12.0/24; 127.0.0.1/8; ::1; };
recursion yes;
additional-from-auth yes;
additional-from-cache yes;
zone "." in {
type hint;
file "/etc/bind/db.root";
};
// put definitions for zones like "localhost" and "127.in-addr.arpa" here
}
// put definitions for real authoritative zones here.
Mail for some reason is not delivering to outlook.com
Find your namservers.
#cat /etc/resolv.conf nameserver 69.xx.xx.xx nameserver 69.xx.xx.xx
– in this case the example is 69.xx.xx.xx
$ dig MX outlook.com @69.xx.xx.xx
; <<>> DiG 9.9.2-P2-RedHat-9.9.2-3.P2.el5 <<>> MX outlook.com @69.64.66.11
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 19033
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;outlook.com. IN MX
;; Query time: 2 msec
;; SERVER: 69.64.66.11#53(69.64.66.11)
;; WHEN: Fri Jan 9 15:38:48 2015
;; MSG SIZE rcvd: 29
[/bash]
There is no result. Now Change to google nameservers. (8.8.8.8 or 8.8.4.4 )
[bash]
~]$ dig MX outlook.com @8.8.8.8
; <<>> DiG 9.9.2-P2-RedHat-9.9.2-3.P2.el5 <<>> MX outlook.com @8.8.8.8
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 33959
;; flags: qr rd ra; QUERY: 1, ANSWER: 4, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 512
;; QUESTION SECTION:
;outlook.com. IN MX
;; ANSWER SECTION:
outlook.com. 17432 IN MX 10 mx3.hotmail.com.
outlook.com. 17432 IN MX 10 mx4.hotmail.com.
outlook.com. 17432 IN MX 10 mx1.hotmail.com.
outlook.com. 17432 IN MX 10 mx2.hotmail.com.
;; Query time: 11 msec
;; SERVER: 8.8.8.8#53(8.8.8.8)
;; WHEN: Fri Jan 9 15:39:26 2015
;; MSG SIZE rcvd: 128
[/bash]