Instructions
Login to your Plesk server.
Select the domain you wish to enable gzip for from the left hand side.
Click in Apache and nginx settings:
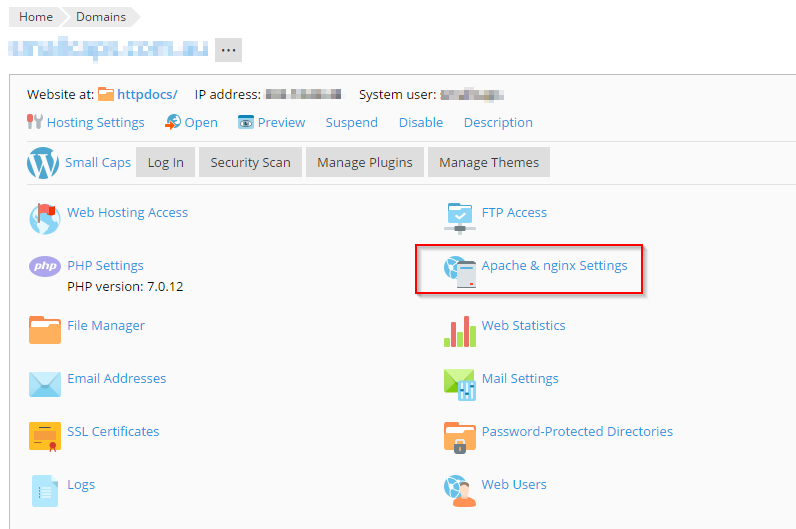
Down the bottom, add the following to the “Additional nginx directives” field:
gzip on;
gzip_disable "MSIE [1-6]\.(?!.*SV1)";
gzip_proxied any;
gzip_types text/plain text/css application/x-javascript application/javascript text/xml application/xml application/xml+rss text/javascript image/x-icon image/bmp image/svg+xml;
gzip_vary on;
Click OK to save.
Verify with GTMetrix.com
Another way is to set up deflate.
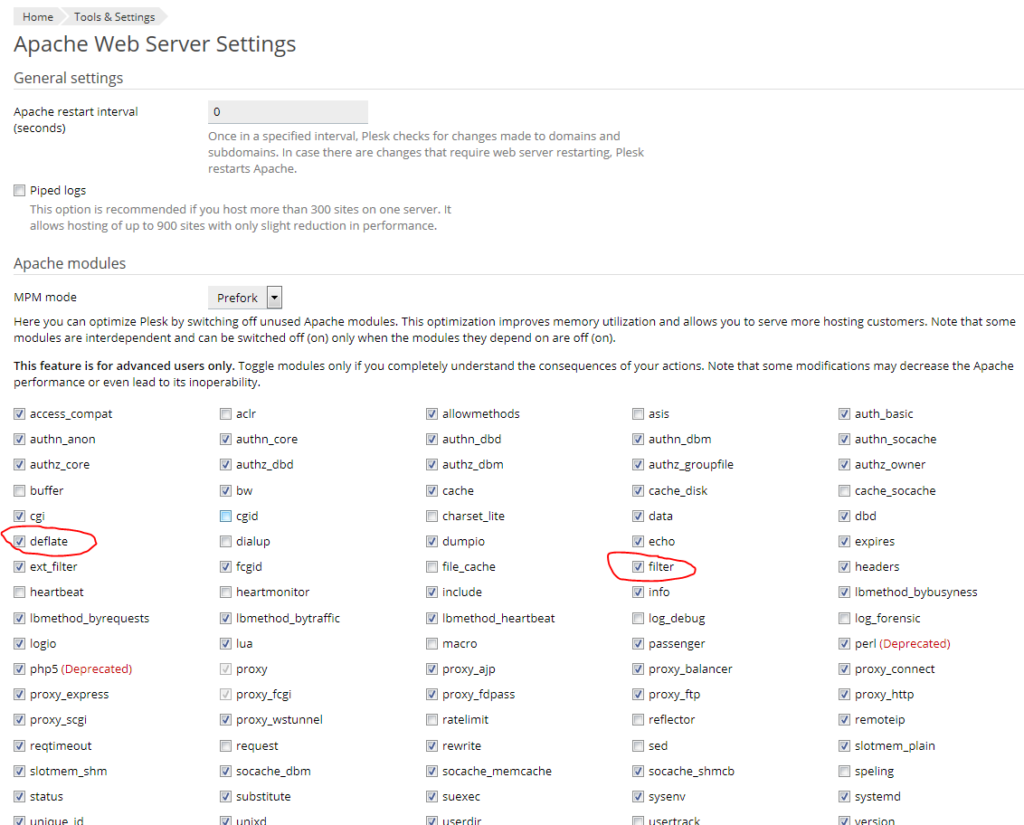
First you need to check the module mod_deflate is enabled on the server.
In plesk:
Or, in ssh:
# httpd -M |grep deflate
Then you need to create the file /etc/httpd/conf.d/deflate.conf
# vim /etc/httpd/conf.d/deflate.conf
and add the following into it.
<ifmodule mod_deflate.c>
AddOutputFilterByType DEFLATE text/html text/plain text/xml text/css text/javascript application/javascript
DeflateCompressionLevel 8
</ifmodule>
Restart Apache
/etc/init.d/httpd restart
Chech here – https://checkgzipcompression.com