Below are listed cPanel and other ports for server administration.
cPanel
cPanel 2082
cPanel – SSL 2083
WHM 2086
WHM – SSL 2087
Webmail 2095
Webmail – SSL 2096
Linux, Windows, Software Tips, Articles and Hacks
Below are listed cPanel and other ports for server administration.
cPanel 2082
cPanel – SSL 2083
WHM 2086
WHM – SSL 2087
Webmail 2095
Webmail – SSL 2096
Generating OpenSSH-compatible Keys for Use with PuTTY
To generate a set of RSA keys with PuTTYgen:
Installing VMware tools in CentOS involves the following steps:
Install the opem-vm-tools:
yum install open-vm-tools
Output:
================================================================================================================================================
Package Arch Version Repository Size
================================================================================================================================================
Installing:
open-vm-tools x86_64 10.1.5-3.el7 base 663 k
Installing for dependencies:
fuse x86_64 2.9.2-8.el7 base 85 k
fuse-libs x86_64 2.9.2-8.el7 base 93 k
libdnet x86_64 1.12-13.1.el7 base 31 k
libicu x86_64 50.1.2-15.el7 base 6.9 M
libmspack x86_64 0.5-0.5.alpha.el7 base 64 k
net-tools x86_64 2.0-0.22.20131004git.el7 base 305 k
pciutils x86_64 3.5.1-2.el7 base 93 k
xmlsec1 x86_64 1.2.20-7.el7_4 updates 177 k
xmlsec1-openssl x86_64 1.2.20-7.el7_4 updates 76 k
Transaction Summary
================================================================================================================================================
Install 1 Package (+9 Dependent packages)
Total download size: 8.4 M
Installed size: 29 M
Reboot the server:
shutdown -r now
Install with with the Vmware CD:
Login to ESXi.
Select the VM from the Virtual Machine list.
Click the actions wheel for the warning message:
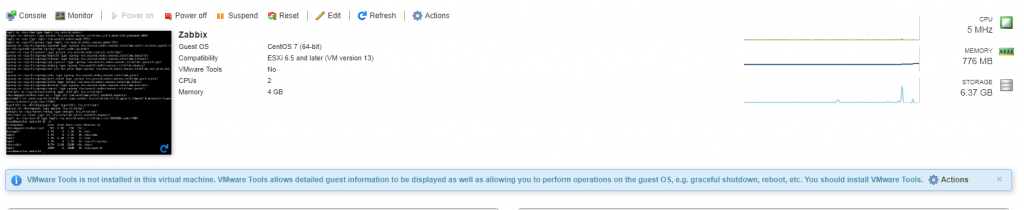
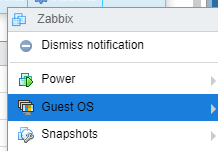
Select Guest OS > Install Vmware Tools
Run the mount command with no arguments to determine whether your Linux distribution automatically mounted the VMware Tools virtual CD-ROM image.
If the CD-ROM device is mounted, the CD-ROM device and its mount point are listed as something like this:
/dev/cdrom on /mnt/cdrom type iso9660 (ro,nosuid,nodev)
If the VMware Tools virtual CD-ROM image is not mounted, mount the CD-ROM drive.
If a mount point directory does not already exist, create it.
mkdir /mnt/cdrom
Some Linux distributions use different mount point names. For example, on some distributions the mount point is /media/VMware Tools rather than /mnt/cdrom. Modify the command to reflect the conventions that your distribution uses.
Mount the CD-ROM drive.
mount /dev/cdrom /mnt/cdrom
Some Linux distributions use different device names or organize the /dev directory differently. If your CD-ROM drive is not /dev/cdrom or if the mount point for a CD-ROM is not /mnt/cdrom, modify the command to reflect the conventions that your distribution uses.
Change to a working directory (for example, /tmp).
cd /tmp
Delete any previous vmware-tools-distrib directory before you install VMware Tools. The location of this directory depends on where you placed it during the previous installation. Often this directory is placed in /tmp/vmware-tools-distrib.
List the contents of the mount point directory and note the filename of the VMware Tools tar installer.
ls /mnt/cdrom/
manifest.txt run_upgrader.sh VMwareTools-10.1.0-4449150.tar.gz vmware-tools-upgrader-32 vmware-tools-upgrader-64
Uncompress the installer.
tar zxpf /mnt/cdrom/VMwareTools-10.1.0-4449150.tar.gz
The value x.x.x is the product version number, and yyyy is the build number of the product release.
If you attempt to install a tar installation over an RPM installation, or the reverse, the installer detects the previous installation and must convert the installer database format before continuing.
If necessary, unmount the CD-ROM image.
umount /dev/cdrom
If your Linux distribution automatically mounted the CD-ROM, you do not need to unmount the image.
Run the installer and configure VMware Tools.
cd vmware-tools-distrib
./vmware-install.pl
open-vm-tools packages are available from the OS vendor and VMware recommends
using open-vm-tools packages. See http://kb.vmware.com/kb/2073803 for more
information.
Usually, the vmware-config-tools.pl configuration file runs after the installer file finishes running. Respond to the prompts by pressing Enter to accept the default values, if appropriate for your configuration. Follow the instructions at the end of the script.
Depending on the features you use, these instructions can include restarting the X session, restarting networking, logging in again, and starting the VMware User process. You can alternatively reboot the guest operating system to accomplish all these tasks.
If you are using vCenter Server, the VMware Tools label on the Summary tab changes to OK.
New: https://support.plesk.com/hc/en-us/articles/213927465
Taking Ownership of Files and Folders in Windows Server. Here are some notes on how to do this:
If you are an administrator, an authorized user, or a backup operator, you can take ownership of a file or folder by completing the following steps:
1. In Windows Explorer, open the file or folder’s Properties dialog box by right-clicking the file or folder and then clicking Properties.
2. On the Security tab, click Advanced to display the Advanced Security Settings dialog box.
3. On the Owner tab, click Edit.This opens the Advanced Security Settings dialog box for editing.
4. In the Change Owner To list, select the new owner.If you’re taking ownership of a folder, you can take ownership of all subfolders and files within the folder by selecting the Replace Owner On Subcontainers And Objects option.
5. Click OK twice when you have finished.
Assigning Ownership
If you are an administrator or the current owner of a file, you can assign ownership of a file or a folder to another user or group by completing these steps:
1. In Windows Explorer, open the file or folder’s Properties dialog box by right-clicking the file or folder and then clicking Properties.
2. On the Security tab, click Advanced to display the Advanced Security Settings dialog box.
3. On the Owner tab, click Edit. This opens the Advanced Security Settings dialog box for editing.
4. Click Other Users Or Groups to display the Select User, Computer, Service Account, Or Group dialog box.
5. Type the name of a user or a group, and then click Check Names. If multiple names match the value you entered, you’ll see a list of names and can choose the one you want to use. Otherwise, the name will be filled in for you, and you can click OK to close the Select User, Computer, Service Account, Or Group dialog box.
6. In the Change Owner To list, select the new owner. If you’re assigning ownership of a folder, you can assign ownership of all subfolders and files within the folder by selecting the Replace Owner On Subcontainers And Objects option.
7. Click OK twice when you have finished.
Codero
Robocopy
Robocopy (Robust File Copy) is a command-line file copying tool included with the Microsoft Windows Server 2003 Resource Kit, free to licensed users of Windows. The tool, as with much of the resource kit, works under Windows XP as well as under the Windows Server platform.
Download Robocopy Command Line Tool for Windows 2003 and 2008 Server / Windows XP / Vista / 7
Please visit Microsoft web site to download Robocopy (rktools.exe – 11.8M). It is part of Windows Server 2003 Resource Kit.
https://www.microsoft.com/en-us/download/details.aspx?id=17657
GUI Tools:
Robocopy GUI is a free GUI frontend to the robocopy command.
RichCopy is a free new utility which offers a number of improvements over Robocopy GUI.
How to tell the network speed of network cards in Linux?
CentOS 7
Find the network cards:
ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens160: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP qlen 1000
link/ether 00:0c:29:d5:dc:4a brd ff:ff:ff:ff:ff:ff
inet 216.55.xxx.xxx/24 brd 216.55.169.255 scope global ens160
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fed5:dc4a/64 scope link
valid_lft forever preferred_lft forever
3: ens192: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP qlen 1000
link/ether 00:0c:29:d5:dc:54 brd ff:ff:ff:ff:ff:ff
inet 192.168.1.101/24 brd 192.168.1.255 scope global ens192
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fed5:dc54/64 scope link
valid_lft forever preferred_lft forever
Ethtool
# ethtool ens160
Settings for ens160:
Supported ports: [ TP ]
Supported link modes: 1000baseT/Full
10000baseT/Full
Supported pause frame use: No
Supports auto-negotiation: No
Advertised link modes: Not reported
Advertised pause frame use: No
Advertised auto-negotiation: No
Speed: 10000Mb/s
Duplex: Full
Port: Twisted Pair
PHYAD: 0
Transceiver: internal
Auto-negotiation: off
MDI-X: Unknown
Supports Wake-on: uag
Wake-on: d
Link detected: yes
# ethtool ens160 | grep Speed
Speed: 10000Mb/s
Script:
for i in $(netstat -i | cut -f1 -d" " | tail -n+3) ; do echo "$i: $(ethtool "$i" | grep Speed | sed 's/Speed://g')" ; done
cat /sys/class/net/<interface>/speed
# cat /sys/class/net/ens160/speed 10000
Above would be in MB.
DMESG
# dmesg |grep eth0 [0.932304] vmxnet3 0000:03:00.0 eth0: NIC Link is Up 10000 Mbps
How to check the raid controller on Linux:
# lspci | grep -i raid 01:00.0 RAID bus controller: LSI Logic / Symbios Logic MegaRAID SAS 2208 [Thunderbolt] (rev 05)
Monitoring Tools
/proc/mdstat
You should get to know /proc/mdstat, looking at it often. This will tell you the state of your arrays, and very importantly it will tell you whether any drives have failed, and whether any arrays are degraded. Check, and check regularly!
xosview
xosview is a venerable utility, and one of the author’s favourites. It is capable of displaying the state of raid arrays, but unfortunately currently the code is broken – it reads mdstat, and doesn’t understand the current output. It is currently (2016) being updated to read the status directly from /sys, and should hopefully soon be able to display raid status correctly. The author leaves xosview running permanently on his desktop to provide an overview of system performance.
mdadm
mdadm –monitor –scan –mail a@b.co.uk
This will fire up mdadm to keep an eye on your arrays. It will daemonize and run in the background, sending an email to the specified address if it detects any problems related to a disk failure. This is good for remote monitoring BUT. It won’t tell you if anything goes wrong with the monitoring! You cannot assume – even if you put this in your boot-up sequence as you should – that you will be notified about important events. It’s not unknown for the daemon to fail.
Don’t rely on this! Check regularly on a manual basis!
smartctl
This tool tells you all sorts of information about your drives. When you read the “When things go wrogn” section, you will see that smartctl is a very important diagnostic tool, but it also provides a lot of proactive information to help you anticipate a drive failure.
There are various S.M.A.R.T. stats that can be looked at which will provide clues:
Attribute | Description |
SMART 5 | Reallocated Sectors Count |
SMART 187 | Reported Uncorrectable Errors |
SMART 188 | Command Timeout |
SMART 197 | Current Pending Sector Timeout |
SMART 198 | Uncorrectable Sector Count |
Backblaze.com (who run huge raid arrays) have a lot of interesting information on their site. They point out that maybe a quarter of their drives fail when all these statistics are 0, so a healthy SMART report does not necessarily mean a healthy drive, but almost none of their drives survive having errors on all five counts.
smartctl also reports on things like drive temperature, how long the drive has been powered on, how many times it has been started and shut down etc. It’s no surprise that drives that get too hot or are otherwise stressed beyond normal limits tend to fail early.
Smartmontools for RAID
https://www.smartmontools.org/wiki/Supported_RAID-Controllers
A good way to check the connectons to mail ports is to use netstat:
# netstat -anp | grep :25 tcp 0 0 0.0.0.0:25 0.0.0.0:* LISTEN 2170/master tcp6 0 0 :::25 :::* LISTEN 2170/master
# netstat -anp | grep :465 tcp 0 0 0.0.0.0:465 0.0.0.0:* LISTEN 2170/master tcp6 0 0 :::465 :::* LISTEN 2170/master
# netstat -anp | grep :587 tcp 0 0 0.0.0.0:587 0.0.0.0:* LISTEN 2170/master tcp6 0 0 :::587 :::* LISTEN 2170/master
I recently added MailEnable to a Windows server and wanted to add SSL. I checked and there is an application that you can use to add the Let’s Encrypt SSL.
Quick Start
Download from https://certifytheweb.com/ and install it.
Click ‘New Certificate’, choose your IIS site (which must have 1 or more hostname bindings set). Save your settings and click ‘Request Certificate’
All done!